Complete Guide on API Security for Mobile Apps | Creative Ground Tech

What is API security?
The world has transitioned to an era of interconnectivity with the Internet of Things (IoT) taking over all phases of everyday human life. And, API is the most common thread that connects all devices and microservices. With the rising popularity and use of API, the cyber risk landscape associated with it has also expanded, pushing further the need for enterprises to focus on API security.
API security refers to the collaborative efforts directed towards safeguarding APIs’ integrity, regardless of them being owned or used. API security encompasses everything spanning from, API access control to privacy, as well as the threat detection and remediation on APIs through API reverse engineering. The phenomenon is centered around securing the application layer to directly address any malicious hacker’s possibilities interacting with the API.
API Security is no longer the sole responsibility of the cloud service providers. App development companies must employ the latest tools and agencies that specialize in performing deep-scanning and threat analysis to ensure the entire app ecosystem remains impenetrable or unexploitable.
Why Is API Security Important?
All businesses rely on APIs to connect their services and also transfer data effectively. The APIs that are broken, exposed, or less secure, attract malicious actors to conduct data breaches.
In case the API connects to any third-party application, all data is ultimately funneled back to the internet. API security includes network security concepts including rate-limiting or throttling, along with related concepts from identity-based security, data security, and information monitoring/analytics. APIs expose sensitive financial, medical, and personal information, which can cost hugely, both in terms of finances and reputation.
API Security Testing comprises of the multiple scanning processes that thoroughly test the server-side of an application. The testing process digs deep to find exploitable flaws or vulnerabilities that can be potentially employed to steal data. Apps use multiple APIs and hence, they usually offer the fastest and easiest entry points to hackers. Any vulnerability, if unpatched, can lead to several severe problems. Incidentally, all apps that rely on the faulty API can then be exploited in a similar manner.
How API Security Automation Is Beneficial?
As service providers expand, so do their APIs increase in number and complexities. New features and services demand their own APIs. Individual APIs are beneficial for app creators as they can selectively incorporate them into their creations depending on the functionalities sought. Additionally, any developer can create an API and even publish it on the internet. Interestingly, there won’t be any resistance or scrutiny when the developer is using public cloud services such as Amazon, Microsoft, and Google.
Manual penetration testing of each service prior to release or production can be a very complex, and time as well as resource-consuming task. In the same manner, manually conducting API Security Testing is very tedious. Not to mention, such a process can significantly delay the move of the service along with the production schedule.
It is imperative to evolve API Security into an automated process. Companies and app developers relying on APIs for the apps and services simply cannot ignore conducting security and penetration testing. Moreover, it is critical that such processes are automated to free up resources and ensure the ecosystem remains impenetrable.
Open Source and Commercial API Security Automation Tools
There are several Open Source (Free) as well as Commercial (License) tools to conduct automated API Testing. However, there are only two major types of API: SOAP (Simple Object Access Protocol), and REST (Representational State Transfer). Hence app developers will have to decide which category of testing tools must be chosen.
It is important to understand the requirement and threats the app and its data will face, before opting for a security testing tool. It is critical the chosen tool conducts the majority of the tests. Otherwise, the entire process can fall short if the testing platform skips out on some of the parametric testing. Additionally, while evaluating the performance and efficiency of the API Security Automation Tools it is important to know how effectively the platform conducts testing and how well it offers a resolution to possible security vulnerabilities.
While there are dozens of Open Source platforms, some of the commonly used include SOAP UI, Postman, Postwoman, Fiddler, Taurus, etc. While these are great tools to conduct automated preliminary API testing, there are a few licensed or paid alternatives that usually offer some more options and benefits. They include ReadyAPI, ACCELQ, REST-Assured, Swagger.io, Katalon Studio, etc.
Challenges of Securing APIs in the Mobile Ecosystem
As discussed earlier, there are several challenges faced while attempting to secure a mobile application. These are compounded by the unavailability of full-fledged standard tools for security testing. Different automation tools are used for mobile apps and web applications altogether despite the fact that many might be using the same backend services and APIs.
Platforms like Appium, Robotium, and Ranorex are common tools in this field. However, it is critical to have a holistic approach that fits the needs and security requirements of an app in the rapidly emerging world of social apps where data flows freely and extensively.
Modern-day apps and the rapidly altering global smartphone app deployment and geopolitics have once again reminded developers about the need to conduct a thorough security audit of the APIs they use. Some of the most common and notorious platforms like Tik Tok and the dozens of other apps that were recently banned are an excellent example. These platforms and their APIs proved just how important is securing APIs in the mobile ecosystem to ensure data integrity and security.
Some of the most common threats in the modern smartphone app ecosystem, especially with the liberal use of APIs, include excessive data exposure, security misconfiguration, improper asset management, poor logging and monitoring, broken or poorly implemented object-level authorization, and inadequate authentication protocols. Add the severe limitation of funds and time, and the trouble becomes very big and concerning.
API Security Best Practices
Organizations need to adhere to specific basic security best practices to employ well-established security controls associated with APIs:
- Prioritize security: Security is a shared responsibility, and not-so-secure APIs can cost a lot. So, organizations need to prioritize on building a culture of API security.
- Proper management: With dozens and hundreds of APIs available publicly, firms need to have a clear vision towards managing them. Conducting regular perimeter scans are useful towards discovering and managing the APIs efficiently.
- Stringent authentication: Most of the public APIs suffer attacks due to non-existent or incapable authorization mechanism. Broken authentication happens when APIs do not enforce authentication or when an authentication factor can be broken easily. APIs are the entry point to any organization’s databases; thus, it’s critical to maintain strict control while accessing them.
- Least privilege access: The foundational security principle to be followed is that the users, programs, systems, processes, devices should be granted only the minimum required access to ace a stated function. And, this should be applied equally to all APIs.
- Traffic encryption: For organizations that have APIs who routinely exchange sensitive data (such as credit card, social security, login credentials, banking information, health data), TLS encryption remains essential.
- Sharing limitation: Organizations are recommended to incorporate advanced scanning tools into their existing DevSecOps processes to restrict accidental exposure of highly secretive information. Enterprises should never expose more data than necessary.
- Validation: Never pass the input from any API through to the designated endpoint without prior in-depth validation.
- Use rate limiting: Setting a well-defined threshold is recommended so that subsequent requests will be rejected in order to prevent denial-of-service attacks.
- Use firewalls: Firewalls enhance web application security by understanding and managing the growing API payloads.
API Security Framework for Your Security Teams
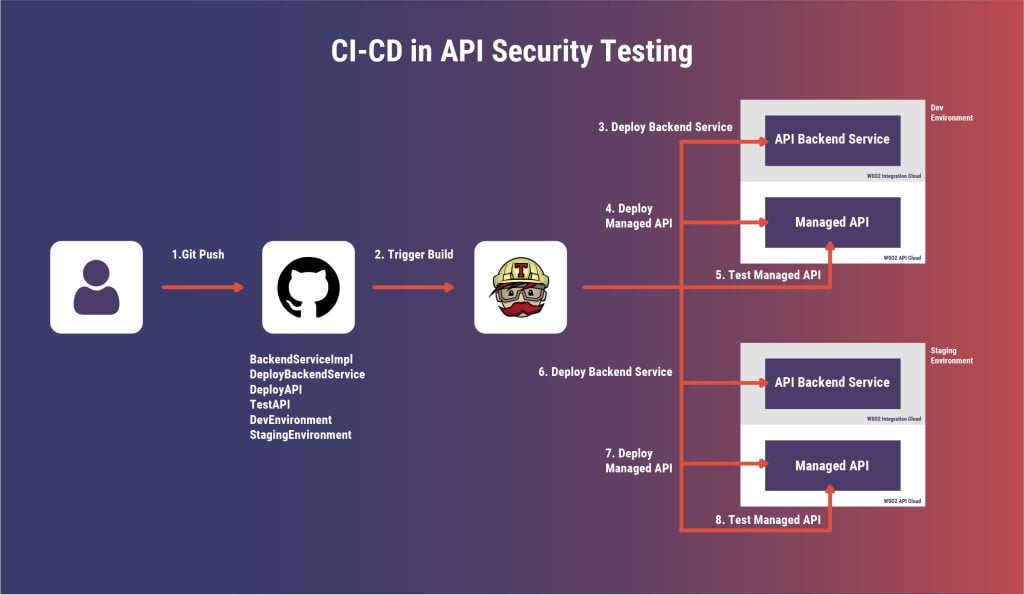
Given the rising threats as well as the increasing use of APIs, every organization needs an API Security Framework. This will ensure that everyone on the team follows a few simple but critical protocols pertaining to the usage of APIs. The framework consists of three steps as below:
1) Continuous API discovery and specification creation.
2) Continuous API specification analysis and inspection.
3) API policy enablement and enforcement.
There is a need to continuously monitor and analyze new as well as old APIs for the many changes and feature additions to understand their current state of specifications. Simply put, it is important to know what the API is doing. An organization using APIs needs to create specifications of all the APIs. Public-facing APIs hosted in the cloud are even more critical. Incidentally, there are tools that can automate the process of discovering new APIs and even track changes to existing APIs.
The next step entitles conducting the right type of security testing such as verifying if the updated API has the right data encryption, is relying on proper authentication and authorization policy, which data sources are being accessed, etc. Such security testing helps prevent data breaches. Incidentally, this is where API Security Automation Tools truly shine as they are able to quickly and dynamically find potential vulnerabilities within the authentication and encryption layers of the API.
The final step is policy creation and enforcement which basically entitles deciding on the two questions:
1. Who should be able to utilize the API?
2. What level of sensitivity, regulatory oversight, and/or privacy concerns does the API have?

Careful management of aspects such as authentication, authorization, encryption, and availability of that API will not only secure the app and data but also potentially eliminate undesired data exposure. Traditionally, API policy enforcement was often done at the network gateway layer. However, modern and dynamic architectures such as mobile and cloud have forced developers to provide the security aspects through SDKs as well as cloud service platform providers’ dashboards.
Why Use Creative Ground Tech for Your API Security
Creative Ground Tech’s fully automated scanners assure an in-depth analysis of web servers, databases, and its implementation for all server components, allowing interaction with the mobile app. The company’s API Security testing solutions excel in the advanced testing of the application’s server-side inside out.
The entire scanning process takes just 20-50 min based on the number of endpoints selected to complete. Creative Ground Tech tests for 20+ test cases in this and some of the typical test cases are Buffer Overflow Vulnerabilities in HTTP Requests, Command Injection Vulnerabilities in HTTP Requests, Cross-Site Tracing Vulnerabilities, Detecting SQL injection and others. Post the API Scan a complete Vulnerability Assessment of the application is achieved, which helps avoid all possible security threats.
Conclusion
With the rapid adoption of cloud, web, and mobile apps, the use of APIs has increased exponentially. Hence the complexity, as well as time and resource restrictions, have forced API security testing to take a completely different phase. Simply put, every business should realize the importance of API security in order to maintain data security and strive to eliminate major security threats. API Security Automation Tools are the ideal solution. The majority of these platforms silently and dynamically monitor for security vulnerabilities and routinely conduct security and penetration testing so that developers can focus on adding new features and fixing bugs.







