For today’s enterprises that are highly dependent on information competitiveness, the importance of information security has no need to be overstated, which is reflected in the increasing information security budget of enterprises every year and the continuous improvement of information security priorities. However, with the continuous acceleration of technological innovation in the information security market, new threats, technologies and methods continue to emerge, and information security talents and professional services are relatively scarce, all of which have brought confusion to the formulation of information security strategies for enterprises.
A good information security maturity model can help enterprises quickly find information security weaknesses and formulate targeted strategies, accelerate the integration of information security into corporate culture, and enhance the “security competitiveness” of enterprises.
Recently, the famous security blog KrebsonSecurity recommended two enterprise information security maturity models and commented as follows:
1. Enterprise Strategy Group Information Security Maturity Model.
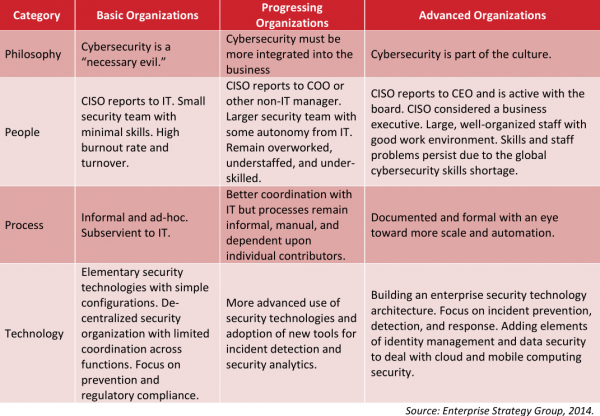
ESG divides the maturity of enterprise information security into three categories: basic, advanced and advanced. At the same time, it provides security planning and strategic paths for the chief information security officer of the enterprise. It is worth noting that ESG believes that security incidents such as data leakage also have positive significance. Usually, major data leakage incidents will stimulate enterprises to upgrade their information security maturity to the next stage.
2. Blue Lava ‘s Information Security Maturity Model

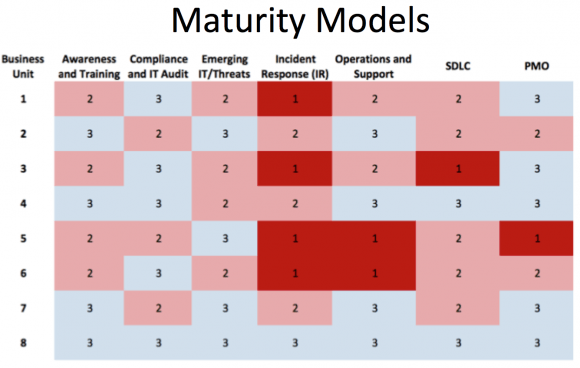
Blue lava divides enterprise information security maturity into three categories and five stages: “defense and treatment”, “compliance-driven” and “risk-based security approach”:
The first stage: The information security process is unorganized or unstructured, and the successful experience of individuals cannot be copied and reproduced, nor can it be extended and promoted. The main reason is the lack of definition and documentation of the process.
The second stage: Information security enters the reproducible stage, some basic project management techniques are formed and can be reused, which is based on the information security process has been defined, established and documented.
Phase 3: Information security efforts focus on documentation, standardization and maintenance of operational support.
Stage 4: Enterprises monitor and control their own information security processes through data collection and analysis.
Stage 5: This is an iterative stage where the company continuously improves information security processes through monitoring and feedback on existing and new processes.
The advantage of the Blue Lava information security maturity model is that it can be customized for all enterprises. Enterprises can establish their own maturity point system for each business department, such as the SDLC (Security Development Life Cycle) and PMO (Project Management) in the figure below. Department), the red block in the figure is the most urgent security shortcoming in the business department of the enterprise.
———————————–
Cyber Security | Creative Ground Tech







