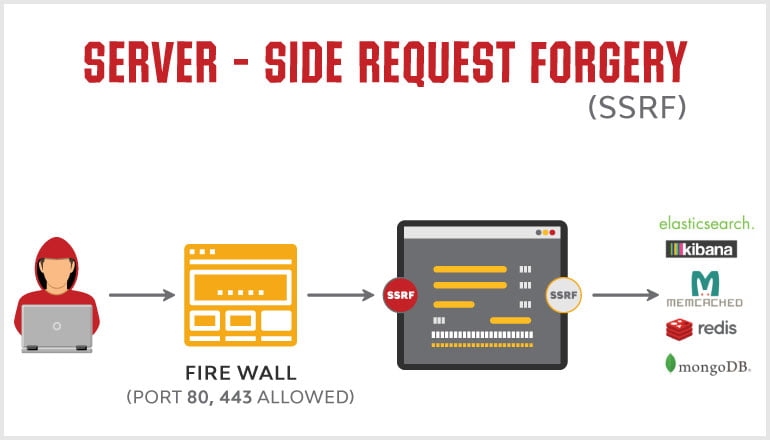
SSRF (Server-Side Request Forgery) is a security loophole constructed by an attacker to form a request initiated by the server. In general, the target of an SSRF attack is an internal system that cannot be accessed from the external network . (Because it is initiated by the server, it can request the internal system connected to it but isolated from the external network )
The reason for the formation of SSRF is mostly because the server provides the function of obtaining data from other server applications and does not Filter and restrict the target address. For example, get the text content of the webpage from the specified URL address, load the picture at the specified address, download and so on.
The SSRF vulnerability is to send a request to obtain resources by tampering with the server, but the server does not find that the request is legitimate, and then the server uses its identity to access the resources of other servers.
for example:
<?php
if (isset($_POST['url']))
{
$content = file_get_contents($_POST['url']);
$filename ='./images/'.rand().';img1.jpg';
file_put_contents($filename, $content);
echo $_POST['url'];
$img = "<img src=\"".$filename."\"/>";
}
echo $img;
?>
This code uses the file_get_contents function to get pictures from the url specified by the user. Then save it on the hard disk with a random file name and show it to the user.
CSRF and SSRF
Literally speaking, the difference between SSRF and CSRF is that it is a request forgery sent by the server, rather than sent from the user. As a trusted user, the server is certainly unlikely to do anything to harm the user. It is a security loophole constructed by the attacker and initiated by the server. Because it is initiated by the server, it can request an internal system connected to it but isolated from the external network. Since the server provides the function of obtaining data from other server applications (such as sharing functions) and does not filter and restrict the target address, it gives the attacker the opportunity to take advantage of it. For example, get the text content of a webpage from a specified URL address, load pictures at a specified address, download resources, and so on. SSRF uses a flawed web application as a proxy to attack remote and local servers.
Summary
In general, CSRF is that the server does not strictly control the data submitted by the user, causing the attacker to use the user’s Cookie information to forge the user’s request and send it to the server. The SSRF is that the server trusts the user-provided controllable URL address too much and has not undergone rigorous testing. As a result, the attacker can use this as a springboard to attack the intranet or other servers.







