We adopt a “Zero Trust Architecture” (ZTA) cybersecurity paradigm.
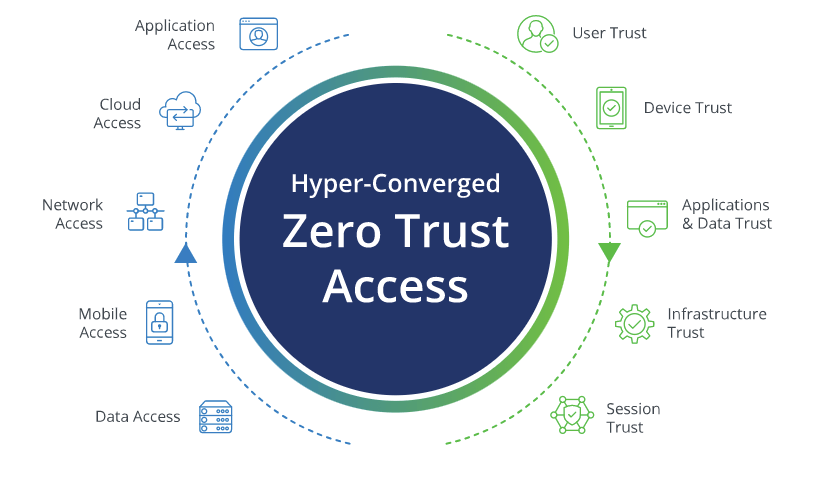
Why? Inadequate access controls can lead to data exfiltration, unauthorized access, lateral movement and/or the introduction of malware into an environment. Consequences of that include damage to brand/reputation, fines, erosion of customer confidence, delays in service delivery due to unplanned downtime, lengthened approval processes and impacts to partner relationships.
So rather than depending solely on using VPNs to access static firewalls to protect all resources within an on-premises network, an end-to-end, “Zero Trust” approach is necessary for operating in public networks.
The term was first popularized by Forrester industry analyst John Kindervag in 2010. In 2020 NIST published 50-page PDF: Special Publication SP800-207. It noted that “Industry has not yet coalesced around a single set of terms or concepts to describe ZTA components and operations.”
“Zero Trust” means that we “assume breach”. So network and access are segregated. Each DAAS (Data, Assets, Applications, Services) resource only interacts with entities which are authenticated and authorized by dynamic fine-grained “least privilege” policies, on a per-session basis. Both server resources and endpoints which request services (user, machine, app, etc.) each must also prove its identity, using mutual TLS (mTLS).
“Zero Trust” needs to be all-encompassing in its vigilance. The current state of assets, network infrastructure, and communications are continuously collected for forensics in case of breach and for analysis to improves the “security posture” of each device, user, and enterprise as a whole.
Because service accounts and authorization are tightly coupled with the application, it often makes sense to set up identities and policies as part of the application infrastructure deployment. Delegating this authority to the development team allows it to iterate quickly on application development (the DevSecOps model).
Security Engineer
Here are “Essential Job Functions” based on various job descriptions:
- Apply established and ad hoc processes and techniques to identify, validate, prioritize, and track security risks.
- Identify uncontrolled risks and recommend control improvements.
- Proactively identify security requirement deficiencies.
- Engage business and technology personnel to elicit security requirements.
- Architect and design security control systems to address requirements.
- Operate and monitor established security controls.
- Identify control deficiencies and make appropriate recommendations.
- Ensure that controls are operating effectively; resolve operating discrepancies.
- Review, triage, and prioritize control output.
- Take appropriate action to resolve security discrepancies.
- Identify, evaluate, and recommend new security technologies, techniques, and tools.
- Define, review, and promote information security policies, standards, guidelines, and procedures.
- As compliance subject matter expert, enforce and monitor compliance with internal and external regulations, policies, and standards.
- Establish and promote strategies to ensure that compliance is effectively monitored and enforced.
- Lead/Co-lead internal process improvement initiatives. Provide feedback on processes by offering suggestions.
- Mentor and supervise junior staff in project-level tasks.
- Assist with adherence to technology policies and comply with all security controls.
Education/Experience Requirements:
- Experience must include direct experience in several of the key areas listed: securing networks and systems architecture, design and implementation, secure software assurance, intrusion detection, defense and incident response, security configuration management, access controls design and implementation and security policy and standards development.
- In-depth knowledge of communications protocols (HTTP/HTTPS, SSL/TLS, OAuth, JWT, SAML).
- Experience with Cyber Security tools, including: Configuration Assessment, Log Aggregation, Integrity Verification, Web Application Security Testing, Network Access Control System, Network Intrusion prevention systems, and Endpoint Security Solutions.
- Strong written and verbal technical communication skills.
- Demonstrated ability to develop effective working relationships that improved the quality of work products.
- Should be well organized, thorough, and able to handle competing priorities.
- Ability to maintain focus and develop proficiency in new skills rapidly.
- Ability to work in a fast paced environment.
- In-depth knowledge of more than one Information Security principle and discipline.
Glossary
Cyber Security Acronyms
- Policies – general statements from management
- Standards – specific mandatory security controls
- Procedures – step-by-step instructions
- Guidelines – recommended actions to follow
Definitions: REMEMBER:
- A threat is a potential harmful incident.
- A threat agent (a malicious actor) is an individual or group that can manifest a threat.
- A threat event is a specific instance of a threat
- A vulnerability is a (potentially exploitable) weakness where there is absence of a countermeasure in place.
- An exposure is an instance of being subjected or exposed to losses from a threat.
- A trigger is an event that indicates that a risk has occurred or is about to occur.
- Enticements are apparent flaws deliberately made available for penetration and exploitation.
- Attacks are attempts to violate an organization’s security or privacy
- An exploit is when a threat agent successfully takes advantage of a vulnerability
- A breach is an attack that has been successful in reaching its goal.
- Impact is the magnitude of harm caused by a threat source
- Likelihood (of occurrence) is a weighted factor that a given threat agent is capable of exploiting a given vulnerability
- Level of risk before treatment is the inherent risk
Quantitative risk analysis:
Asset Value (AV) x Exposure Factor (EF) = Single Loss Expectancy (SLE).
Annualized Rate of Occurrence (ARO) X Single Loss Expectancy (SLE) = Annual Loss Expectancy (ALE).
Cost/benefit of implementing a particular safeguard, where
ALE is the annual loss expectancy = (ALE before safeguard) – (ALE after safeguard) – (annual cost of safeguard)
Residual risk = total risk – countermeasures.
CIA triad tenants: +IAAA
- Confidentiality vs. Disclosure (IPSec encryption in transit, social engineering)
- Integrity vs. Alteration (shared among authorized persons or organizations)
- Availability vs. Destruction (RAID-5, DDoS)
- Accountability (auditing)
Privacy Threshold Assessment is used to identify PI and determine how to treat the data.
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) developed at Carnegie Mellon SEI.
Cloud Security Posture Management (CSPM) monitors continuously identifies and remediates cloud infrastructure risks in each cloud service using application programming interfaces (APIs) configuration data against compliance benchmarks. For example, they can ensure logs are being gathered from host operating systems and the network (NetFlow), and that API event logging is turned on.
The newer acronym CIEM (Cloud Infrastructure Entitlements Management) was coined by ermetic.com for their product which ensures that identities (both human and machine) do not have excessive permissions that can be exploited by threat actors or malicious insiders.
Jericho Commandments
https://collaboration.opengroup.org/jericho/commandments_v1.2.pdf define the 11 areas and principles that must be observed when planning for a de-parameterized future in cloud environments.







