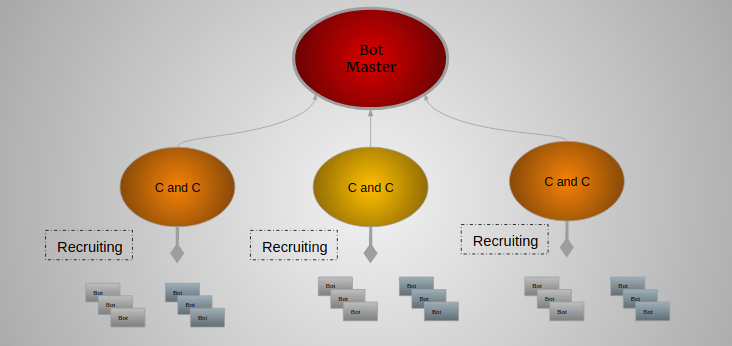
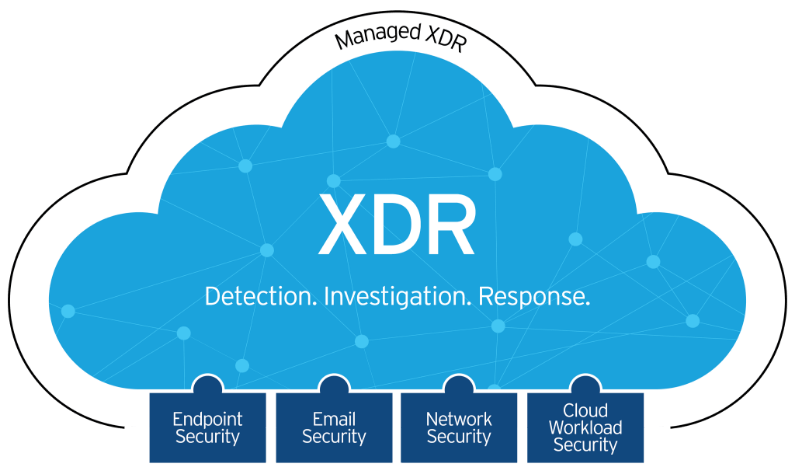
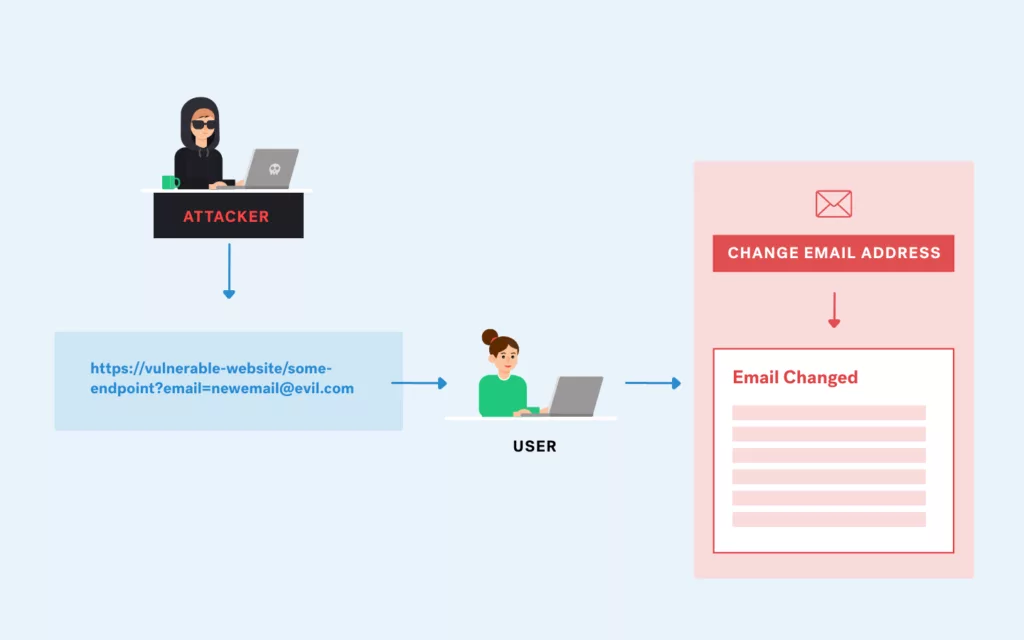
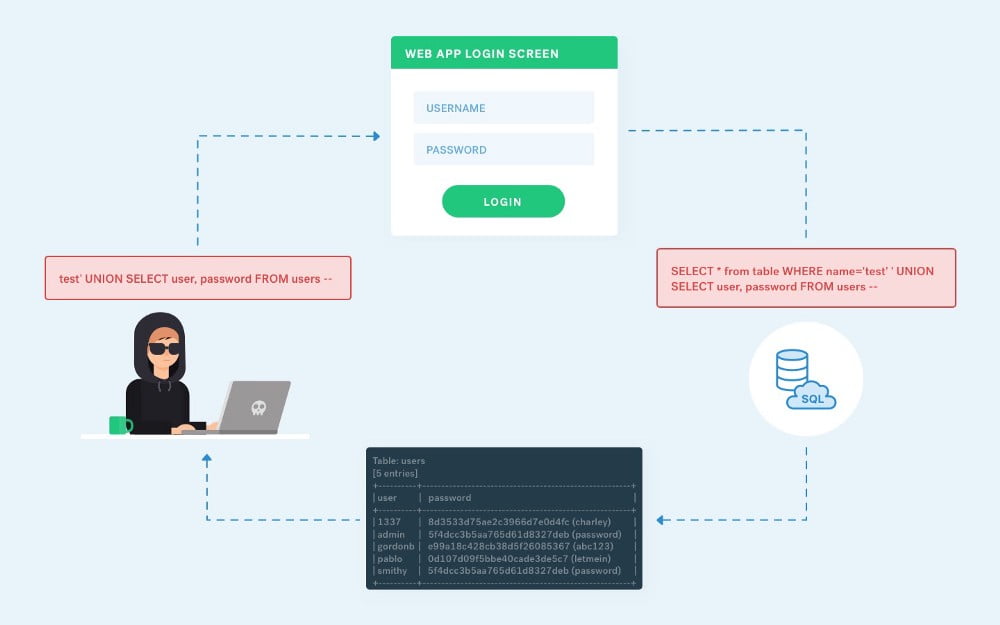
C2: Command and Control Explained
A successful cyberattack is about more than just getting your foot into the door of an unsuspecting target. To be of any real benefit, the attacker needs to maintain persistence access within the target environment, communicate with infected or compromised devices inside the network, and potentially exfiltrate sensitive data. The key to accomplishing all these […]
C2: Command and Control Explained Read More »