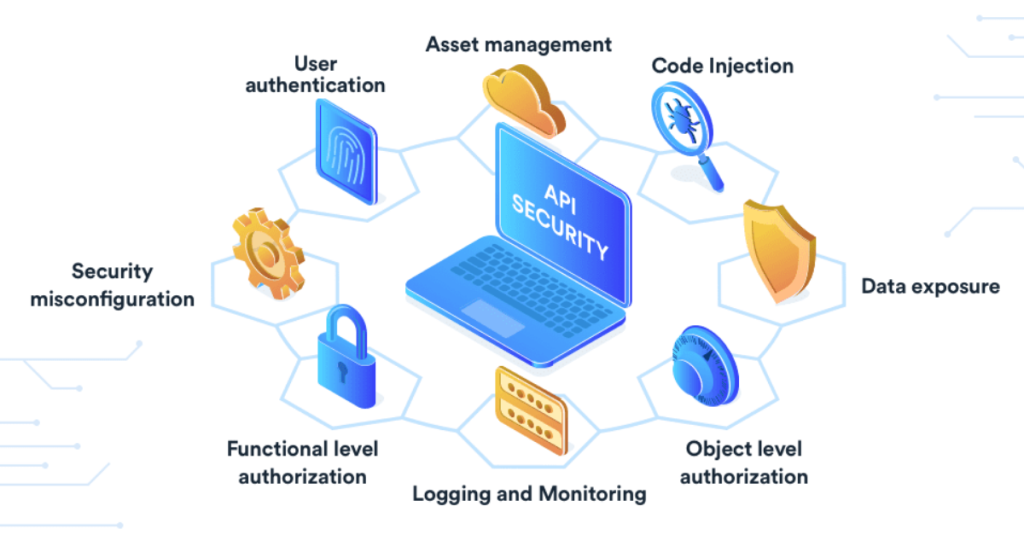
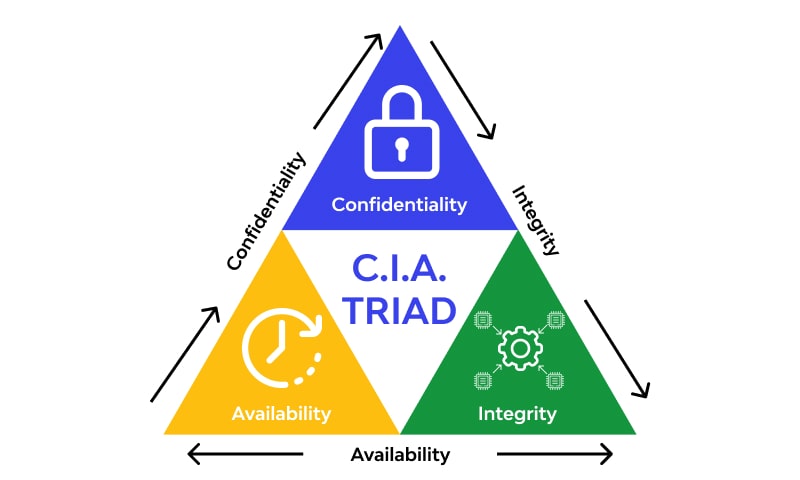
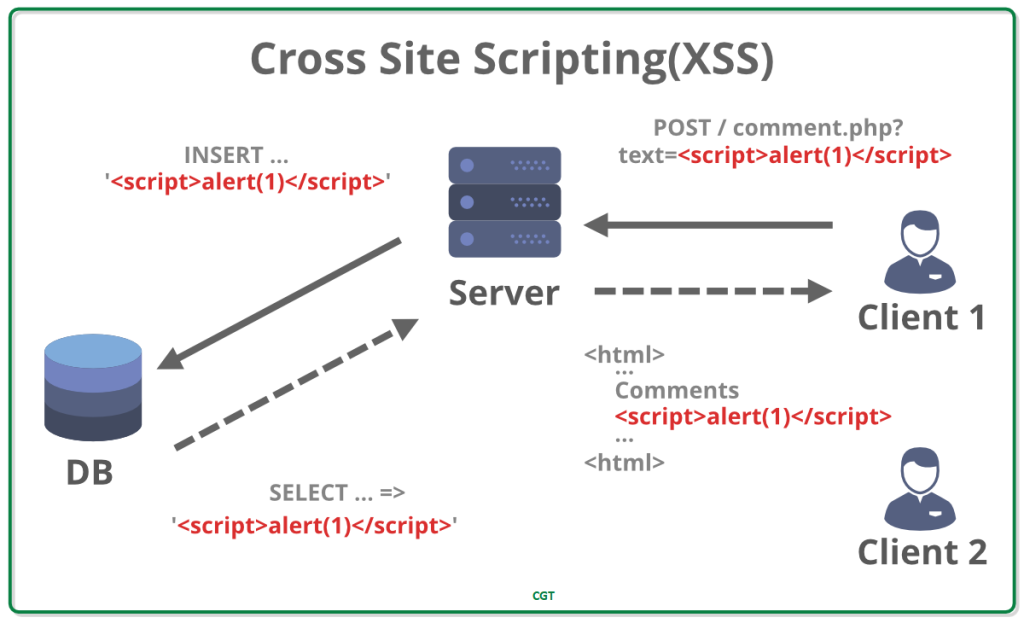
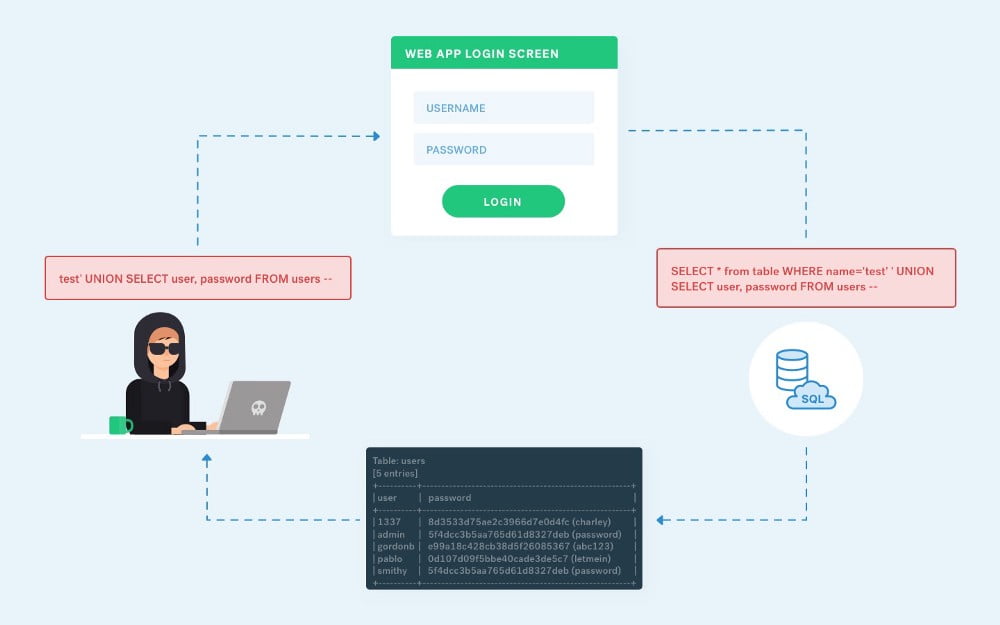
The OWASP API Security Top 10
API security Refers to the measures and practices employed to protect APIs (Application Programming Interfaces) from security threats and vulnerabilities. APIs act as a bridge between different software systems, allowing them to communicate and share data. However, they can also become targets for attackers seeking to exploit vulnerabilities and gain unauthorized access to sensitive information […]
The OWASP API Security Top 10 Read More »