API Security | Applications
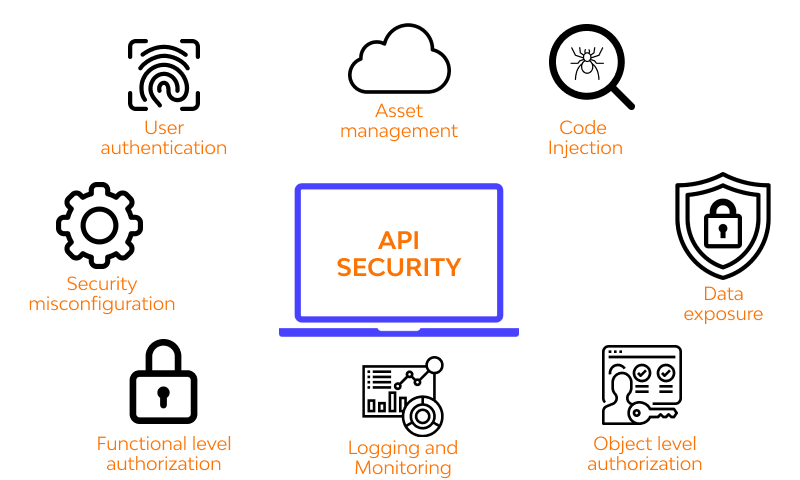
Complete Guide on API Security for Mobile Apps | Creative Ground Tech What is API security? The world has transitioned to an era of interconnectivity with the Internet of Things (IoT) taking over all phases of everyday human life. And, API is the most common thread that connects all devices and microservices. With […]
API Security | Applications Read More »